Text / Sina Finance and Economics e observation (WeChat public number: sinaeguancha) columnist Yang Yanqing Lin Chunjie (authors are the first deputy editor of the first financial and the vice president of the first financial and economic research institute) The government should learn from it, but it cannot be overcorrected. The reason for the rise of digital currency is partly related to public concerns about the phenomenon of foreign currency in various countries. The central bank and the government should face this problem and take steps to restore public confidence, but in the process can not be overkill. Crimes, money laundering and terrorism promoted by technological advances are increasingly difficult to detect and stop from behavior, and the lack of a global response mechanism has exacerbated this situation. As long as the crime has a motive of interest, its behavior can be traced by means of money. To ensure that the currency can be tracked may be the last bastion in the face of the ever-increasing use of technology to build illegal and criminal networks around the world. If we let the digital currency based on encryption technology detach from the regulatory system, all efforts will fall short. Global policymakers need to jointly initiate the regulation of digital currency, and should learn from it. It is the public's concerns about the current credit currency system that has created the soil for digital currency breeding. Digital currency, like a mirror, can reflect the problem, but it is not the solution. As Apple CEO Cook recently advised at MIT's speech: What humans need to worry about is that machines are becoming more and more like humans, but that humans are becoming more and more like machines. Humanity, humanity, and economic and social order require fair and far-sighted rules and guardianship, even though the rules themselves are difficult to perfect. 1. Opened Pandora's Box Advances in technology have made most people feel that there is no more privacy, and personal information, preferences, destinations, and consumption are all exposed to the data center. At the same time, people are beginning to feel uneasy while enjoying the convenience and ubiquitous service they bring, but they are helpless. The massive WannaCry (also known as Wanna Decryptor) ransomware that broke out in May 2017 showed us the tip of the iceberg of the terrible future of this side of the coin. WannaCry gives people a new perspective on cybercrime and digital currency bitcoin based on distributed networks. For the first time, many people have heard of the existence of darknet. This matter can be summarized as follows: A government-developed "cyber weapon" was stolen by anonymous hackers, and stolen cyber weapons flowed into the dark network and were difficult to track; one (or several) people obtained (or purchased) from the darknet anonymously. The cyber weapon attacked computers all over the world, and extorted a certain amount of encryption and was difficult to find out the digital currency of the destination; to some extent, the attack lost control, so that a large number of public facilities became the target of the attack, and In the general understanding, only cyber warfare between countries will involve these goals, and smart criminals will try to avoid these goals and avoid the fierce counterattack of the irritated government. 2. Submerged network world: surface network, deep network and dark network The ransomware has made the dark net a new buzzword, so what is this? We divide the real-world network into Surface Web and Deep Web, while Darknet is part of the Deep Web. The deep network corresponds to the surface network, which is the Internet that most people are exposed to. If the Internet world is likened to a sea, then the indexed networks that can be searched by search engines (Google, Baidu, or Bing) are surface networks. Underneath, deep network, deep network resources are not indexed, and can not be searched using conventional search engines. It is unclear how big the deep network is in theory, but it is widely estimated that the size of the deep network is much larger than that of the surface network. The number of deep web sites may be 400 to 500 times that of the surface network, and the largest 60 deep web sites store data almost 40 times that of the entire surface network (Daniel Sui, 2015). Formal institutions will also set up their own websites in the Shenzhen Open, such as the Library of Congress, the US Census Bureau and the economic data website Freelunch.com. In addition, instant messaging servers also exist in the deep network. Darknet is part of the deep network and the fastest growing segment. In general, the dark network refers to the part of the deep network that exchanges data through the distributed network in an anonymous manner. Unlike the shallow network and most of the deep networks, most of the dark networks can only be accessed anonymously. The dark network relies on encryption technology, and the technology has no distinction between good and evil. The behavior of many users of the dark network is not necessarily illegal. For example, reporters exchange information through the dark network, and those who are worried about being persecuted by the government also use dark networks to disseminate information. Ont routing (Tor) is one of the main means of logging in to the dark network anonymously. Each computer connected to the onion router can set up a website. People can connect to this site but don't know where they are. The US Naval Research Laboratory is the inventor and disseminator of onion routers. The US government continues to develop and promote technology in the anonymous field. In 2010, Onion Server also received the 2010 Annual Social Welfare Free Software Award from the Free Software Foundation. In addition, garlic routing "I2P" (anonymous network project, which belongs to dynamic distributed network) is also becoming more and more popular. The design philosophy is to not trust any party in the network, all data is encrypted. 3. Out of control dark world: crime, drugs, money laundering and terrorist trading Advances in network technology are splitting the world into two forms: on the Internet side, people feel that they are always stared at by an invisible eye; on the other hand, we can hide deeper than ever before. The dark net allows everyone to hide behind the mask, where we can see what the world looks like after losing its restraint. The closure of the Silk Road on October 1, 2013 is an enlightenment for many people to understand the dark net. The goal of Ross Willian Ulbricht, nicknamed "Fearing Pirate Robert", when he founded the Silk Road website in 2011, was to create an online crime market that could not be seized by the government. In the following period, the Silk Road website became famous, and it was hailed as Amazon and Ebay in the drug industry. Like other online shopping platforms, on the Silk Road, merchants are also subject to buyer reviews, including product quality, logistics time, and more. But the difference is that the customer does not actually access the real address (IP address) of the merchant through the anonymous server, and vice versa. It took the US Federal Bureau of Investigation (FBI) a long time to figure out the actual controller of this well-known website. After the Silk Road website was finally closed, the FBI judged that the Silk Road had a total volume of more than $1.2 billion (calculated at the current price of Bitcoin) by June 2013, with more than 150,000 anonymous users and approximately 4,000 Left and right suppliers. Dark-network-based crimes are not limited to drugs, and they do not converge after the Silk Road is closed. These crimes include buying murders, paying for human slaughter, sex trades, child pornography, illegal document transactions, and so on. List and price of sales services in some darknets in 2016: An hour of DDOS attacks $5; 1% of the fee is issued with proof of bank assets; $90,300,000 km of aviation credits; $30 for an American Express card; $238 for a French driver's license, if you need a German or American driver's license, you only need $173; $400 to learn how to invade an ATM The $20 online tutorial will teach you how to use DDOS attacks with the ability to crack WIFI. Source: 2016 underground hacker marketplace report Source: Balduzzi M. , Ciancaglini V (2015) Source: Balduzzi M. , Ciancaglini V (2015) Bakak Pasdar, the legendary hacker, Bat Blue's chief executive, once mentioned an accident in his research that showed how talented people can look at crimes in a game-like mindset, such as murder. Pasdal gave an example: some websites offer bonuses through crowdfunding, and those who want to get the money need to upload evidence to prove that they have executed a murder. Dark nets don't just serve crime, they also promote crime. In terms of population share, Australia is the country with the highest drug use rate in the world. Ten percent of drug users interviewed in the country have used dark nets to buy drugs in the past year, a large proportion of which are men under the age of 25. Those who buy drugs from the dark net use a higher dose of drugs on average. Money laundering and the acquisition of weapons by terrorists through dark nets have also allowed these acts to expand in ways that were previously unimaginable. 4. Global cybercrime and forward-looking supervision The annihilation of the hacker forum darkode may be one of the most well-known cases in the illegal websites of countries to check the dark network, and more than 20 countries participated in the operation. The forum is a dedicated communication place for hacker organizations lizard squad. It is also a place for cybercrime transactions. Hacking tools, botnet tools, 0day vulnerabilities, malware programs, stolen credit cards, and spam services are all available. But the involvement of these governments is only a case. So far, the mainstream trend of the government and the public has been very cautious about the investigation of the dark network, which is considered to touch the bottom line of personal privacy or trade secrets. In fact, they largely recognize the existence of this technology. Coupled with the cooperation of countries in this field are also scruples, which makes it difficult to combat the crimes based on dark net crimes. “Regulators initially closed their eyes on the dark net. In fact, they provided the basic weapons needed by the dark net to a large extent.†The hacker Ghost Elephant said, “Now they It’s hard to say that there is a fundamental change in attitude. Even if they change, it is difficult to reverse this trend. Technology spreads like weeds, and the government does not have an advantage." "Ghost Elephant" is committed to chasing criminal behaviors that exist in the dark net. He invades the sale of child pornography websites through "pollution" documents, and then traces the pedophiles in turn. But he admits, "In the beginning, the government had an advantage, and now the profits brought by criminal behavior have built up a towering firewall, they have the best genius, we can say that we lost the best time." In 2015, Europe arrested five members of the criminal gang using the famous online banking Trojan Zeus, but only a month later the botnet brought a more sinister function back. After the onion router began to compromise with the US government several times, the more "safe" garlic routing became the choice of more dark web sites. The dark-net market is increasingly developing into the appearance of traditional organized crime. According to Joe Van Buskirk, a researcher at the National Center for Drug and Alcohol Research (NDARC) in Australia, because of the anonymity of the onion network system, people don't have to worry about the law and anything can be sold. "When I first entered this market, I was shocked. These sites look very formal, just like eBay, I think anyone can use it very easily." 5. How to deal with technical violence? Dark nets are breeding crimes, but this is not the whole of technology in the field of crime. If an important part of the past to stop crime is to monitor the execution of crime and label possible criminal tools, then encryption-based technology will make these efforts go to waste. Controlling the sale of firearms can limit the incidence of crime and the spread of terrorism. The traditional method is to limit the production and circulation of firearms, and to find the source of firearms through ballistics to deter crime. Soon, ordinary 3D printers can print out guns using ordinary consumables. After the crime is destroyed, it can be like it has never appeared, then how to stop these behaviors? Another example is new drugs. At present, cheap synthetic drugs are becoming popular. UNODC (UN office for drugs and crime) has found that the number of newly synthesized psychotropic substances (Psychoactive substances) reported to them increased from 26 kinds in 2009 to more than 500 kinds in 2015. The driving force behind it is a huge benefit. If the new drug of the future can be printed out through a home printer, the transaction is only a procedure of “burning after useâ€, how will we deal with it? The development of technology is pushing humanity from the era of "strength and violence" to the era of "technological violence." In the era of "strength and violence", the institutions with the strongest strength have control. Even those organizations that have already been very large and organized criminals are hard to compare with the government supported by the people and mastering the state machine. But now the situation is different. The people who have the best technology have already had the right to do whatever they want, while others can only let it be slaughtered. The advantage is not always on the side of the people. The Australian National Center for Drugs and Alcohol Research said in a report that the agency’s Drug Trends Project has been tracking the drug trade in the dark market since 2013. They found that in the dark market, there are often different forces. The behavior of attacking the server against each other. These include technical geniuses for extorting online drug trafficking websites that are also difficult for the government to shake. 6. Currency is the last bastion Even if all the crimes are hidden in the dark, one end will be exposed to the water, as long as their actions are profit-driven, and most of the behavior is true. In most cases, criminal behavior brings real wealth, its behavior makes sense, and money is the only medium. Money is a general equivalent, a contract between the owner and the market about exchange rights. The currency must be valuable and needs to be recognized by more and more people. The legal currency after the gold and silver era has fallen, and the issuance of widely recognized currencies (banknotes) has always been a privilege of the government. These currencies can be tracked. Technically, the currency issued by the government can determine why and why. So for a long time, how to make the currency brought by illegal activities become legal income has been and is increasingly a problem for criminals. But digital currency is changing all of this. Many people may think that the unscrupulous use of the coinage by the government has led to the rise of digital currency, which makes sense, but it cannot be a reason for refusing to supervise the digital currency. Paying attention to privacy has become a symbol of civil society, but order is the basis for maintaining the functioning of civil society, and the support of order is the price of transparency, traceability and crime, whether it is for individuals, businesses or governments. The publication of ruling information constrains the behavior of the government; in addition to paying attention to the country, the enterprise also includes penalties for fear of tax evasion; the biggest concern when individuals commit crimes is that behavior may be discovered and eventually punished; individuals and organizations gain After illegal income, the existence of the global anti-money laundering network cannot be “realizedâ€; terrorism is not only difficult to obtain funds and weapons, but also always fears of being annihilated. However, imagine: What would a world like doing wrong and criminal behavior difficult to track? Dark nets and encryption-based digital currencies that are immersed in the dark are becoming huge markets and catalysts for the upcoming "technical violence" era, even for ordinary crimes. One month after the “Silk Road†was closed, “Silk Road 2.0†was launched. After being destroyed, the “Silk Road Reloaded†website using the I2P anonymous network was born. The only thing that has not been shaken is its means of payment, and in fact it has been expanded. The “Reborn Silk Road†not only accepts bitcoin for payment, but also supports eight other different encrypted digital currencies. The total market value of digital currencies has grown dramatically over the past few years. As of June 7, 2017, the global market capitalization of digital currencies exceeded $100 billion. In less than half a year in 2017, bitcoin rose. More than twice. Chinese investors have made a huge contribution to the soaring price of digital currencies such as Bitcoin. In 2016, China's bitcoin transactions accounted for 93% of global transactions. Source: First Financial and Economic Research Institute Source: CoinMarketCap The encryption function of digital currency is not because their transaction process is confidential. In fact, due to the characteristics of distributed networks, their transactions are more open than any other currency. This secrecy is based on anonymity (as long as you don't link personal information to the digital wallet), which means that tracking the circulation of digital currencies is difficult, but still feasible. Some services are working to make up for this "vulnerability". For example, Easycoin's service content is to return bitcoin to you through a large number of micro-transactions, making it more difficult to trace its circulation. Source: Balduzzi M. , Ciancaglini V (2015) Digital currency is bringing changes to the world, many of which are positive. To a certain extent they constitute a containment for the government and give the people another choice, but that doesn't mean they don't need to be regulated. One of the core reasons is that anonymous, untrackable, unregulated digital currencies can make technical crimes a closed loop, money laundering and terrorism are popular, and disappear into inexplicable bit bytes, but their effects are hurting. Everyone in this world. If every penny of blackmail is tracked, does the person who initiated the WannaCry ransom virus have enough motivation and courage to attack the world? 7. Is the digital currency a currency? assets? Still something else? There is a problem to be solved before we actually start acting. That is what exactly bitcoin is? currency? monetary assets? Anything else? Or nothing. The answer to this question will determine what action we take. Money is a contract between the owner and the market about the right to exchange. A common currency requires four functions: the transaction medium, the unit of account, the value of storage, and the deferred payment standard. Digital currencies such as Bitcoin have now played a role in some trading media; they have not done well in accounting units, and in their trading scenarios they are more used to pay than to price, even in most illegal transactions. In this way, in terms of storage value, it is not possible to draw conclusions about the rise and fall of other currencies over time in the digital currency. Another possibility after the skyrocketing may be a plunge, especially in the case of price manipulation; the last function is to postpone payment. From the current point of view, there is no major debt contract with digital currency as the repayment method, or the digital currency-based debt is issued. Another simpler way to judge is that we did not mention inflation when talking about digital currency. It’s just the rise and fall of the digital currency for other currencies. So the digital currency is not a currency, at least not yet, and even the connection to the near currency is not. To be bold, with the current structured digital currency as the foundation of the global monetary system, it will only lead to a disastrous end: global deflation and the Great Depression. So is the digital currency a financial asset? The answer is also vague. Financial assets are intangible assets whose value is determined by means of contracts. For example, the stock is a contract to determine the company's ownership certificate, which ensures that the equity owner can share the company's future earnings; the bond is that you have the right to recover the principal and interest. Digital currency does not seem to be a financial asset, but people have begun to use its ICO (Initial coin offering), similar to an IPO. So what exactly is the digital currency? It may be a “new speciesâ€, but its impact is so great that we cannot ignore it and take no action. 8. What should the regulator do? For supervision, this is a very difficult situation, because regulators can not apply the established regulatory principles, but this is not unsolvable, and humans are not facing this situation for the first time. First, regulators should develop regulatory principles based on the characteristics of the digital currency. Since digital currency has crossed national borders, global collaboration is a must, and the G20 should do something about it. Second, tracking and enhancing transparency is the direction of regulation. But this does not mean that digital currencies need to give up their main features, such as their basic mining methods. Third, because digital currency has been used as a trading medium, even if it is not a real currency, anti-money laundering rules must include digital currency due to the embarrassing trend of dark networks, crime and terrorism. Fourth, if we assume that digital currency is a financial asset, then those basic regulatory rules applicable to financial assets such as information disclosure, investor protection, etc. should be the basic requirements of ICO and other actions. Fifth, specifically for China’s digital currency trading platform, the lingering circumvention of foreign exchange controls, money laundering risks and terrorist threats, combined with the destruction of the balance of “mine mining machinesâ€, makes it possible to master advanced mining machines and a large number of bitcoin dealers. Already formed the ability of market manipulation, the trading platform has only one hole leading to the darkness, and the rationality of existence has been lost. Finally, the government should learn from it, but it cannot be overkill. The reason for the rise of digital currency is partly related to public concerns about the phenomenon of foreign currency in various countries. The central bank and the government should face this problem and take steps to restore public confidence, but in the process can not be overkill. Digital currency has its own characteristics, but from the current point of view, there is no substitute for legal currency. Digital currency is like a mirror of real money. It reflects fundamental problems, but brings more problems. solution. (The author of this article: Deputy Editor-in-Chief of the First Financial Daily) Women'S Jackets,Short Women'S Jackets,Summer Women Jacket,Women Puffer Jackets Shaoxing Haisa Textile And Garment Co.,Ltd , https://www.haisafashiones.com Why do we need to regulate digital currency?
Why do we need to regulate digital currency?  Figure 1 Where do you see the network?
Figure 1 Where do you see the network? 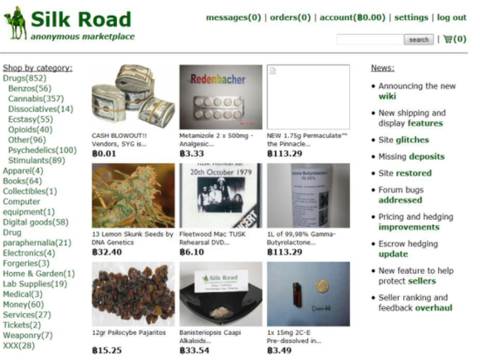 Figure 2 Silk Road webpage screenshot
Figure 2 Silk Road webpage screenshot 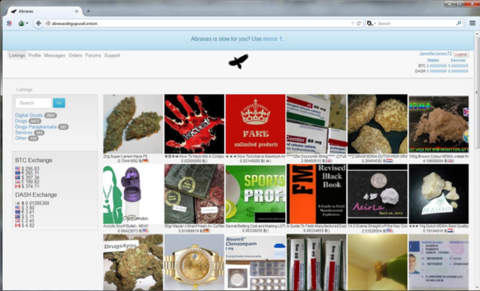 Figure 3 Typical onion server-based network black market website
Figure 3 Typical onion server-based network black market website 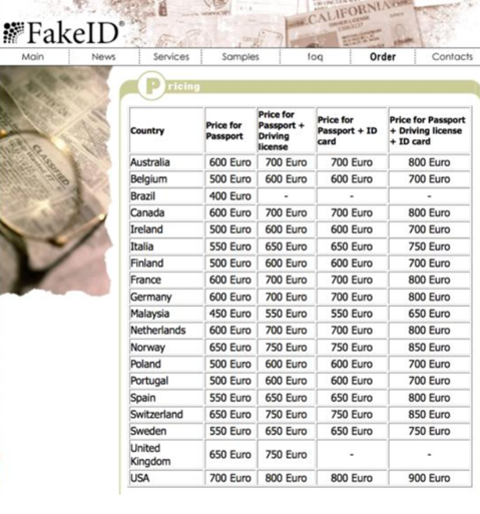 Figure 4: False documents with clearly marked prices
Figure 4: False documents with clearly marked prices 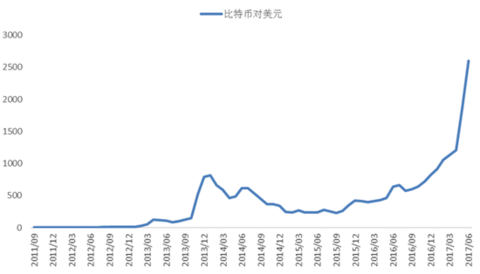 Figure 5 A sharp rise in bitcoin prices
Figure 5 A sharp rise in bitcoin prices 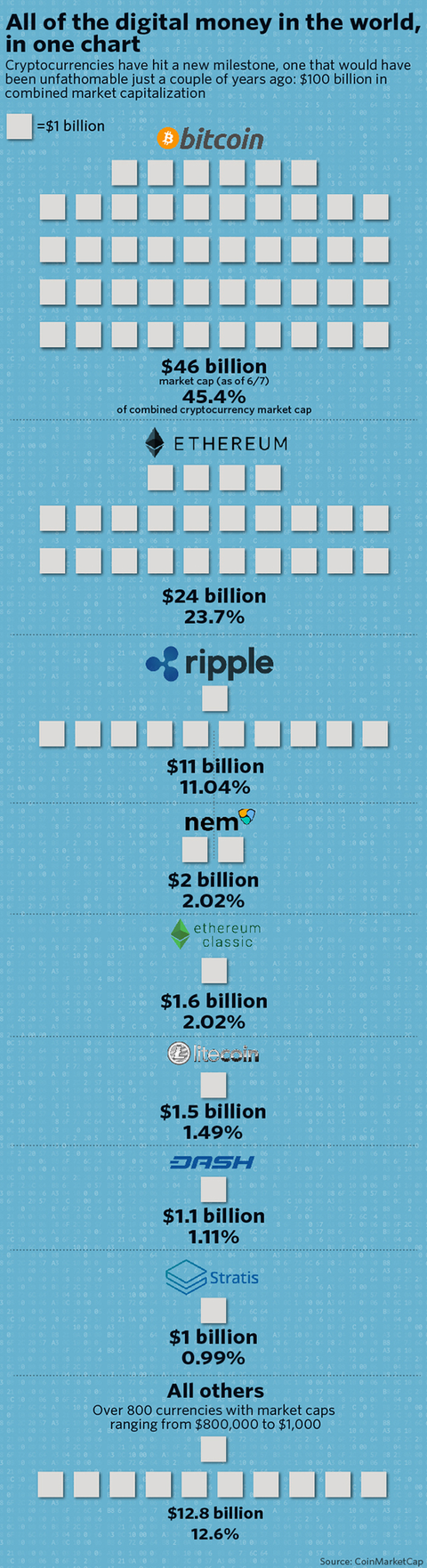 Figure 6 Global digital currency total market value exceeds 100 billion US dollars
Figure 6 Global digital currency total market value exceeds 100 billion US dollars  Figure 7 Easycoin dedicated to enhancing digital currency transaction encryption
Figure 7 Easycoin dedicated to enhancing digital currency transaction encryption 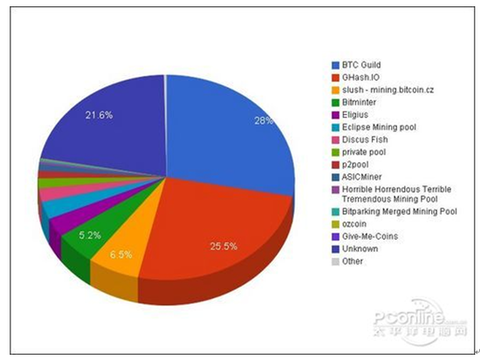 Figure 8. Bitcoin is concentrated in several "mine pools"
Figure 8. Bitcoin is concentrated in several "mine pools"